This challenge presents us with three levels of reverse engineering, a lot of CTFs have this same concepts therefore you will have a good basic understanding on how to tackle some of the beginner to intermediate challenges.
Task 1 -> Debugger
Is it recommended to install the debugger radare2.
Task 2 -> Crackme1
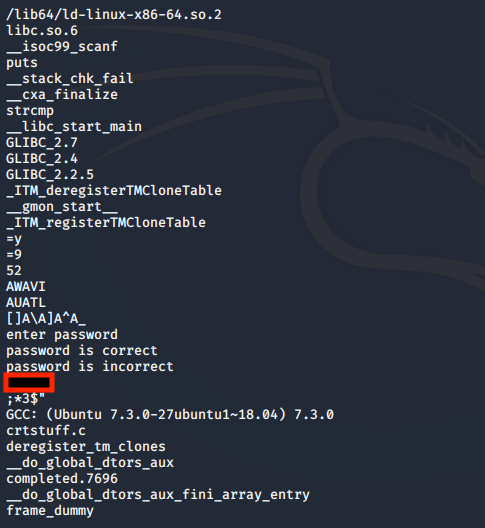
The first file asks for a password, the first step with such a challenge is to use the command strings and have a look if the password is hardcoded in the file.
strings crackme1.bin
Task 3 -> Crackme2
The next file also asks for a password, but this time we can not discover it by using the strings command. Inspecting the file with Binary Ninja we see that the cmp instruction is called. Let’s check if it is comparing our input against ‘0x137c’.
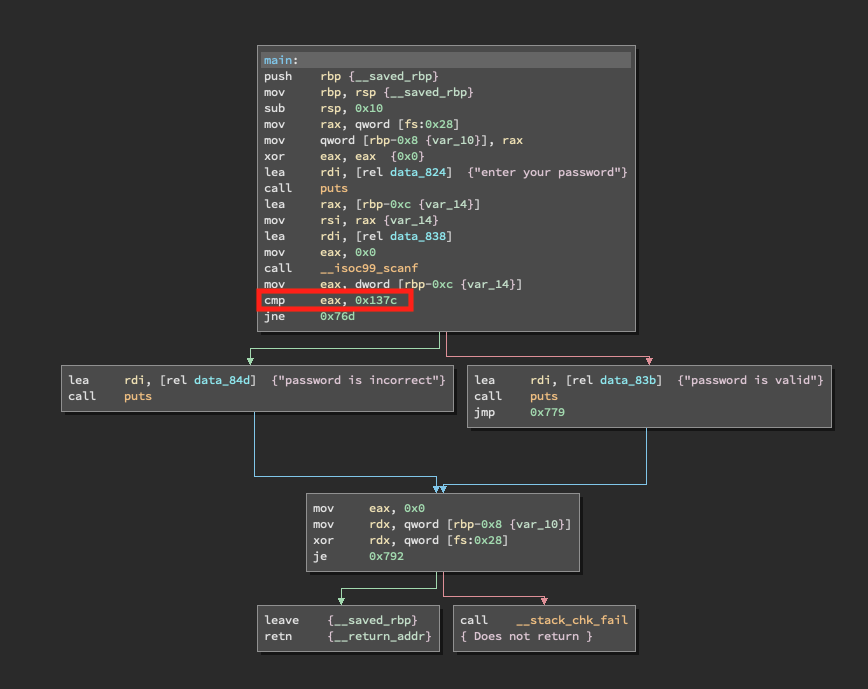
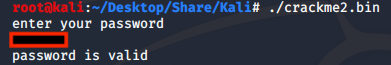
After a quick google search on what the decimal value of ‘0x137c’ is we can use it as a password and check if our assumption is correct.
Task 4 -> Crackme3
The last file presents us with a more complicated challenge. We could more a static analysis as we did before, here tools such as ghidra or ida would be beneficial since they provide a high level view of the assembly code.
We will be performing dynamic analysis with the help of gdb.
To install gdb, use the following command.
sudo apt install gdb
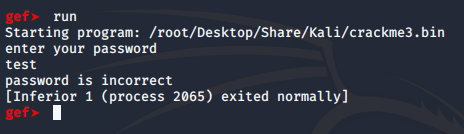
Once installed, let’s open our file with gdb and run it inside gdb.
gdb crackme3.bin
run
Since this challenge also asks for a password, we will focus on the cmp instructions. Let’s have a look at the main function.
disassemble main
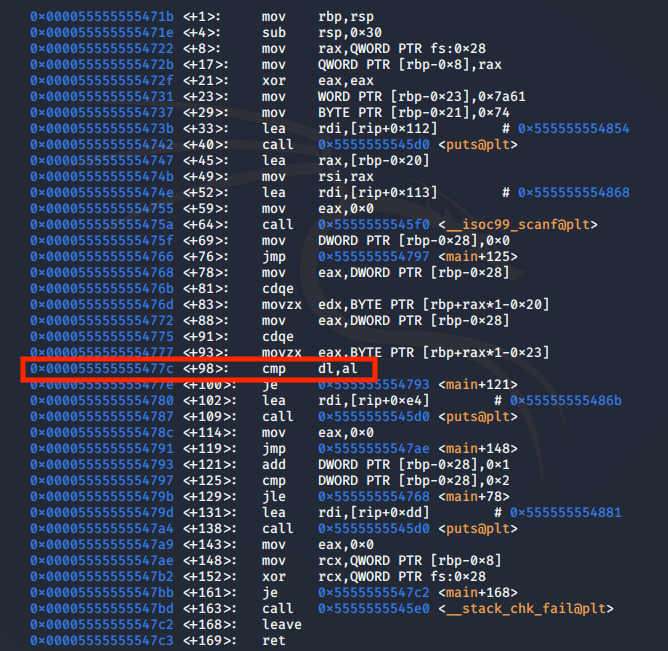
This cmp instruction is the moment the program compares our input with the password. We can check the variables at runtime and discover the password.
First, we need to set a breakpoint.
break *0x000055555555477c
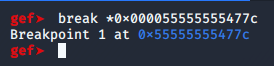
The breakpoint will stop the program when it reaches that instruction and we will be able to see what each register contains.
Run the program and supply it with a random password.
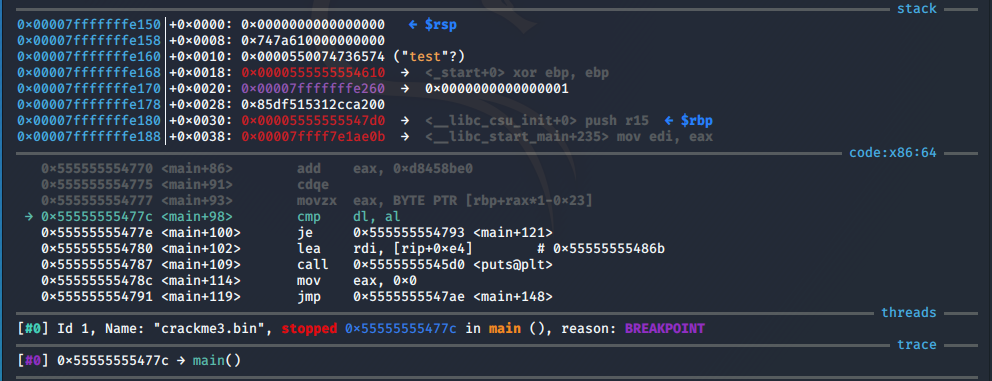
Now that we are at the breakpoint let’s examine both ‘dl’ and ‘al’
print $al
print $dl
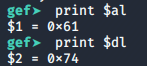
We discover that ‘al’ contains 0x61 which represent the value ‘a’ as for ‘dl’ contains 0x74 representing the value ‘t’. We used the password ‘test’ therefore the program is comparing the first character of our input with the first character of the password.
We now know that the password starts with ‘a’ let’s repeat the process, but this time use ‘atest’ as a password.
Note: When the program is stopped at a breakpoint you can use the command ‘continue’ or ‘c’ to continue executing the program.
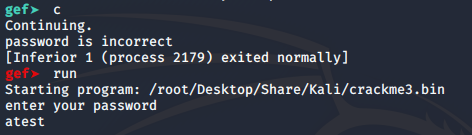
Keep examining the variables at the breakpoint and you will discover the full password.